American democracy runs on trust, and that trust is cracking. Nearly half of Americans, both Democrats and Republicans, question whether elections are conducted fairly. Some voters accept election results only when their side wins. The problem isn’t just political polarization—it’s a creeping erosion of trust in the machinery of democracy itself. Commentators blame ideological tribalism, … Read More “How Cybersecurity Fears Affect Confidence in Voting Systems” »
Category: voting
Auto Added by WPeMatico
Technology and innovation have transformed every part of society, including our electoral experiences. Campaigns are spending and doing more than at any other time in history. Ever-growing war chests fuel billions of voter contacts every cycle. Campaigns now have better ways of scaling outreach methods and offer volunteers and donors more efficient ways to contribute … Read More “The Voter Experience” »
It’s possible to cancel other people’s voter registration: On Friday, four days after Georgia Democrats began warning that bad actors could abuse the state’s new online portal for canceling voter registrations, the Secretary of State’s Office acknowledged to ProPublica that it had identified multiple such attempts… …the portal suffered at least two security glitches that … Read More “Problems with Georgia’s Voter Registration Portal” »
Andrew Appel shepherded a public comment—signed by twenty election cybersecurity experts, including myself—on best practices for ballot marking devices and vote tabulation. It was written for the Pennsylvania legislature, but it’s general in nature. From the executive summary: We believe that no system is perfect, with each having trade-offs. Hand-marked and hand-counted ballots remove the … Read More “On Secure Voting Systems” »
Last month, I convened the Second Interdisciplinary Workshop on Reimagining Democracy (IWORD 2023) at the Harvard Kennedy School Ash Center. As with IWORD 2022, the goal was to bring together a diverse set of thinkers and practitioners to talk about how democracy might be reimagined for the twenty-first century. My thinking is very broad here. … Read More “Second Interdisciplinary Workshop on Reimagining Democracy” »
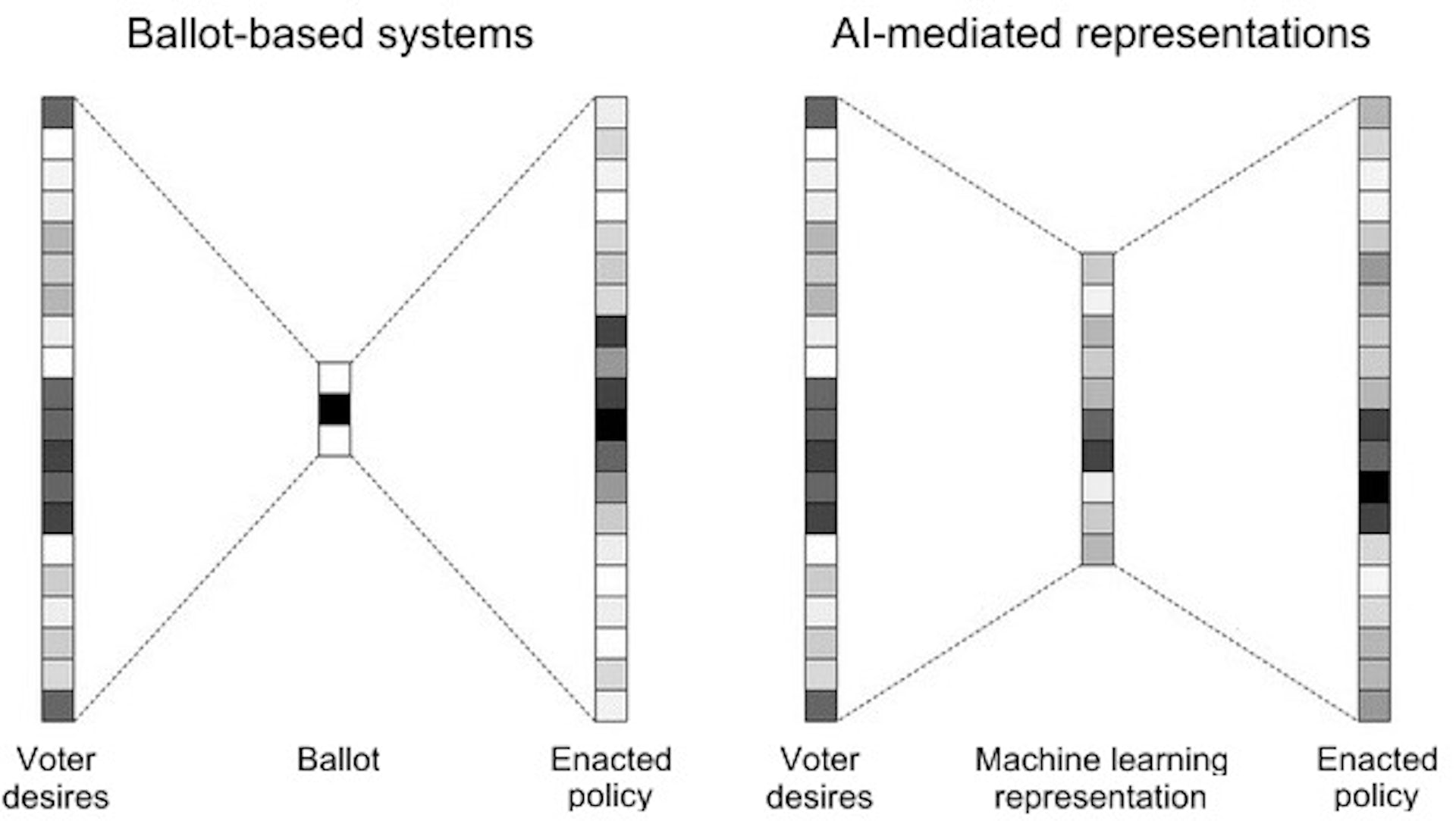
Artificial intelligence is poised to upend much of society, removing human limitations inherent in many systems. One such limitation is information and logistical bottlenecks in decision-making. Traditionally, people have been forced to reduce complex choices to a small handful of options that don’t do justice to their true desires. Artificial intelligence has the potential to … Read More “AI and Lossy Bottlenecks” »
Interesting analysis: This paper discusses the protocol used for electing the Doge of Venice between 1268 and the end of the Republic in 1797. We will show that it has some useful properties that in addition to being interesting in themselves, also suggest that its fundamental design principle is worth investigating for application to leader … Read More “Security Analysis of a Thirteenth-Century Venetian Election Protocol” »
If an AI breaks the rules for you, does that count as breaking the rules? This is the essential question being taken up by the Federal Election Commission this month, and public input is needed to curtail the potential for AI to take US campaigns (even more) off the rails. At issue is whether candidates … Read More “AI and US Election Rules” »
Online voting is insecure, period. This doesn’t stop organizations and governments from using it. (And for low-stakes elections, it’s probably fine.) Switzerland—not low stakes—uses online voting for national elections. Andrew Appel explains why it’s a bad idea: Last year, I published a 5-part series about Switzerland’s e-voting system. Like any internet voting system, it has … Read More “Security Vulnerability of Switzerland’s E-Voting System” »
Well designed and well timed deepfake or two Slovakian politicians discussing how to rig the election: Šimečka and Denník N immediately denounced the audio as fake. The fact-checking department of news agency AFP said the audio showed signs of being manipulated using AI. But the recording was posted during a 48-hour moratorium ahead of the … Read More “Deepfake Election Interference in Slovakia” »